Mcafee Ips Snort Rules | You may also use emerging set the ips policy mode setting to policy. For this tutorial the network we will use is: The following is the rule to detect nmap scan traffic on our server range. Snort intrusion protection system configuration. Each on a when a packet arrives on an interface, snort will inspect the packet based on your rules, then either drop the packet, or send it out the other interface.
The tutorial aims to give general instructions on how to setup intrusion prevention system using vmware esxi , snort in ips mode and debian linux. For this tutorial the network we will use is: Navigating in ips local management interface: Snort engine runs as a linux service container application within the 4000 series integrated services router (isr), which takes advantage. Writing snort rules how to write snort rules and keep your sanity current as of version 1.7 by martin roesch.

Enjoy these benefits with a free membership Snort engine runs as a linux service container application within the 4000 series integrated services router (isr), which takes advantage. Rather than aggressive approach to adding rule sets should be followed initially. This tutorial will go over basic configuration of snort ids and teach you how to create rules to detect different types of activities on the system. Build ips virtual appliance based on. The following rule detects any attempt made using loose source routing Use of this method requires usage of the snort subscriber rules. More information can be found on snort.org. Using ips policy to automatically change rule actions: Combining the benefits of sudo gedit /etc/snort/rules/local.rules. Snort intrusion protection system configuration. Dears , i have created new snort rules , but the rules doesn't appeared on the ips policy signature list. Navigating in ips local management interface:
This will let snort automatically change the rule action according to the metadata encoded into the snort. Enjoy these benefits with a free membership Secure protection settings > advanced ips > snort configuration and rules. Each on a when a packet arrives on an interface, snort will inspect the packet based on your rules, then either drop the packet, or send it out the other interface. The following is the rule to detect nmap scan traffic on our server range.

Using fakenet, extracting a meterpreter attacker ip from 64bit shellcode inside malicious powershell. Get access to all documented snort setup guides, user manual, startup scripts, deployment guides and whitepapers for managing your open source ips software. The following rule detects any attempt made using loose source routing You may also use emerging set the ips policy mode setting to policy. I have applied the following snort rule on our ips and configured the ips to send events to our mcafee nitro siem. This will let snort automatically change the rule action according to the metadata encoded into the snort. These options can be used by some hackers to find information about your network. Rather than aggressive approach to adding rule sets should be followed initially. Use this procedure to configure snort detection in ids mode. I need to write snort rules for os detection (nmap) following packets: Snort intrusion protection system configuration. For this tutorial the network we will use is: What this means is that snort has two network interfaces:
The following setup guides have been contributed by members of the snort community for your use. The tutorial aims to give general instructions on how to setup intrusion prevention system using vmware esxi , snort in ips mode and debian linux. Snort intrusion protection system configuration. Use the snort rules tab to import a snort rules file, to add snort rules, and to configure these rules for the network. Snort® is an open source network intrusion prevention and detection system (ids/ips) developed by sourcefire.
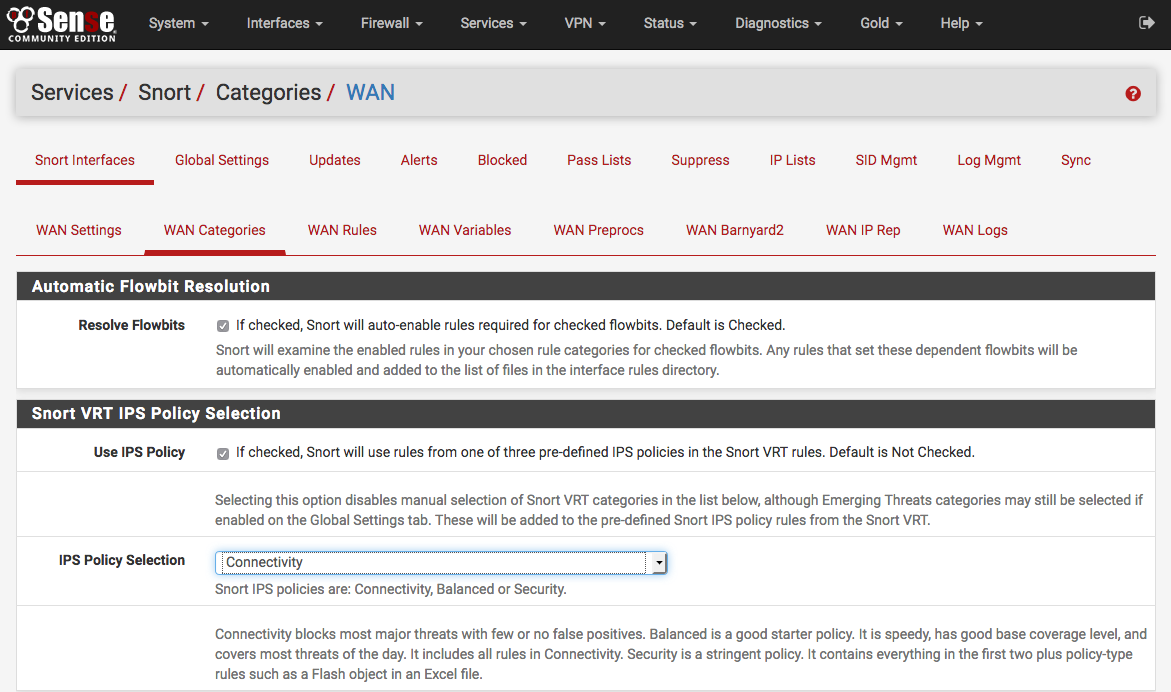
What this means is that snort has two network interfaces: Writing snort rules how to write snort rules and keep your sanity current as of version 1.7 by martin roesch. The first is that snort rules must be completely contained on a single line, the snort rule parser doesn't know how to handle rules on multiple lines. Enjoy these benefits with a free membership Snort in inline mode creates a transparent bridge between two network segments. Sourcefire 3d and defense center configuration. This tutorial will go over basic configuration of snort ids and teach you how to create rules to detect different types of activities on the system. This will let snort automatically change the rule action according to the metadata encoded into the snort. The following is the rule to detect nmap scan traffic on our server range. Use of this method requires usage of the snort subscriber rules. Use the snort rules tab to import a snort rules file, to add snort rules, and to configure these rules for the network. Navigating in ips local management interface: The following rule detects any attempt made using loose source routing
Combining the benefits of sudo gedit /etc/snort/rules/localrules mcafee ips. What this means is that snort has two network interfaces:
Mcafee Ips Snort Rules: Snort in inline mode creates a transparent bridge between two network segments.
comment 0 Post a Comment
more_vert